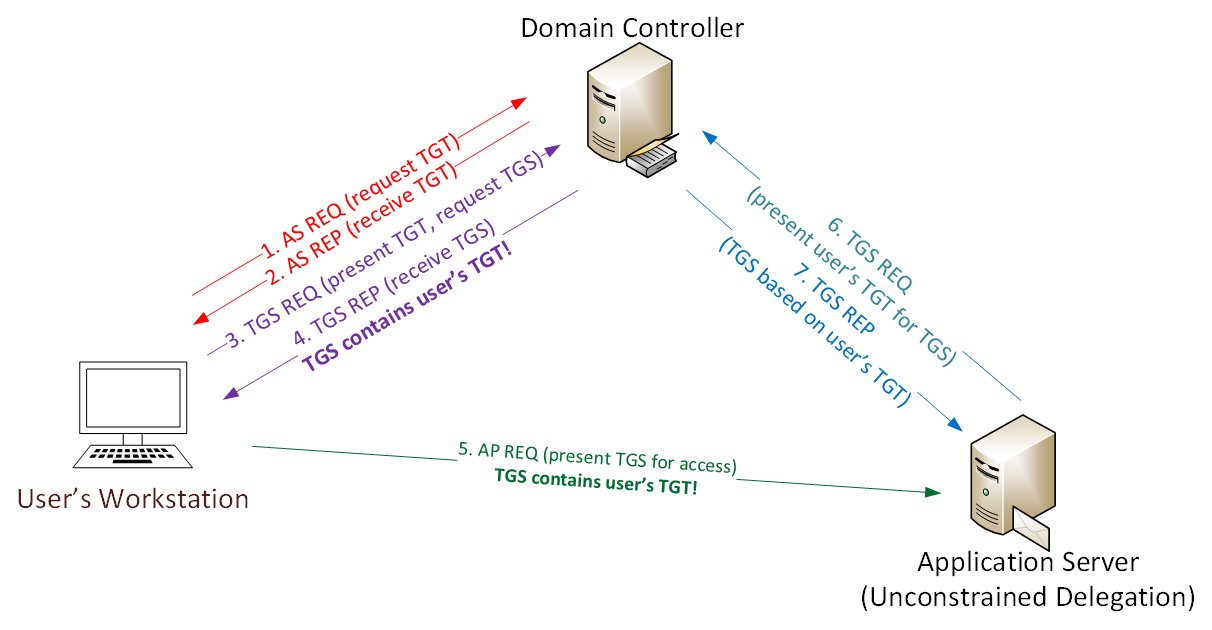
Active Directory Security Risk #101: Kerberos Unconstrained Delegation (or How Compromise of a Single Server Can Compromise the Domain)
At Black Hat USA 2015 this summer (2015), I spoke about the danger in having Kerberos Unconstrained Delegation configured in the environment. When Active Directory was first released with Windows 2000 Server, Microsoft had to provide a simple mechanism to support scenarios where a user authenticates…
adsecurity.org
重點在於When the user’s service ticket(TGS) is provided to the server for service access, the server opens the TGS and places the user’s TGT into LSASS for later use. The Application Server can now impersonate that user without limitation!
可用下面的PowerShell查詢AD上有那些Account有Unconstrained Delegation權限
dsquery * domainroot -filter "(&(objectCategory=user)(userAccountControl:1.2.840.113556.1.4.803:=524288))" -attr cn .....看你要輸出那些屬性說是有漏洞, 但其實要利用也沒有這麼容易:
第一個你要攻破有Unconstrained Delegation帳號所在的伺服器(因為要下一步要使用mimikatz從LSASS抽出TGT而後使用Pass-The-Ticket攻擊), 再來還要引導高價值目標連線進來使用綁定Unconstrained Delegation權限帳號所啟動的Application.
只能說這個攻擊一旦就緒, 事後即使進行數位鑑識取得證據, 也會難以拼湊出跡證到底屬於哪些帳號所為. 基於這點好處, 這手法對攻擊者來說算是十分有價值吧.
補充資料們:



